Do any of the below statements ring a bell to you?
- We are extremely worried about the need to constantly update and get rid of weak passwords in the organization.
- As an organization, we need to safeguard business critical data from insiders as most data breaches happen with the assistance of an insider.
- Worried about suspicious activities and want to take a controlled approach to tackle it.
- We want to include multiple steps of authorization including a three step authentication method or finger print scanning.
If you are worried about any of the above statements to secure your critical data, then you have come to the right place. For any or all of the above statements, we have three words for you – Identity and Access Management (IAM).
So, Identity and Access Management (IAM) is the best possible option to make sure that the right individuals have the access to the resources they require in order to do their day-to-day tasks. Having an IAM system in place reduces the workload or the necessity to have a manual IT administrator to manage employee access on applications. Using the Oracle Cloud Infrastructure IAM tool, you can manage the restrictions to be imposed on access for certain teams/employees and to which particular tools.
In this blog, we will discuss Oracle IAM and everything that you need to know about IAM components.
What is Oracle Identity & Access Management?
Oracle Cloud Infrastructure Identity and Access Management (IAM) is a unique product mostly used to increase security and productivity. This is done by ensuring the management and automation of identity lifecycles, offering controlled access to identities to software and hardware stack in the organization.
The history of Oracle IAM dates back to 1999 when the first product in this stack was introduced by the company as a part of Oracle Internet Directory. In the last 20+ years, Oracle has improved and offered a wide range of IAM features like single sign-on, directory sync and directory administration control etc. The brief history of Oracle’s venture into IAM features tells us how important this tool is for enterprises and what steps Oracle has taken to provide solutions with the evolution of technology over the years.
What is the need for Identity & Access Management Solution?
Enterprises leverage the Oracle IAM solution for enhanced data security and to reduce manual workloads which improves business productivity.
Basically, the IAM tool helps you protect organizational data against any cybersecurity attacks. Moreover, it also establishes a consistent governance of access and identity management in the organization. When an employee’s role within a team is changed, the corresponding changes are automatically reflected with IAM.
Data Security – Data security is an area of concern for most enterprises dealing with potentially hundreds or thousands of employees. A single breach in password or email hack can jeopardize the security of the organization. The whole idea of using the IAM solution is to constantly monitor and ensure the safe practices are followed around the organization.
Business Productivity – The benefit of having an IAM solution in your enterprise makes it easier for the people to manually enter passwords and the need or urge to write it down. IAM logs in the employees according to their access and provides them the right tools to work with. This significantly reduces the manual tasks administered by an IT team and can help in improving business productivity.
If the access rights are not managed efficiently, the enterprise is at a major risk and can be vulnerable to cyber attacks. In order to safeguard your organization against data threats, it is a must to include an IAM solution.
What can be achieved using Identity and Access Management?
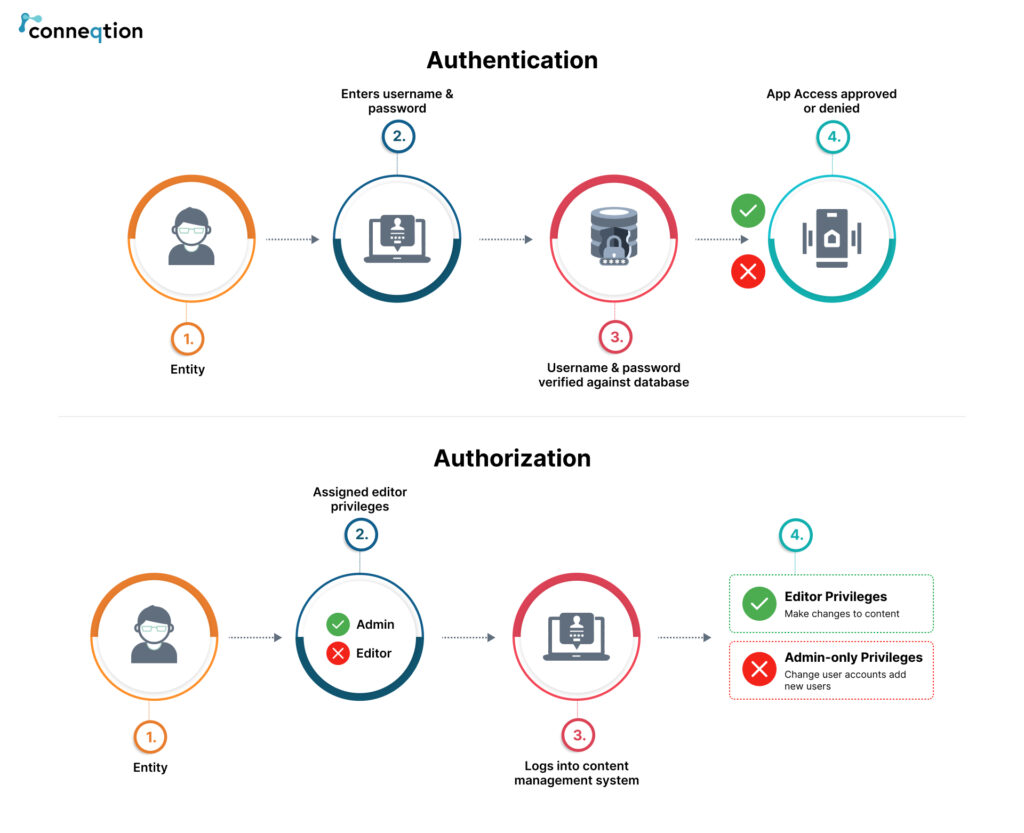
Authentication and Authorization Process
If you are looking for an individual role-based access control for your IT team, IAM solutions can come to your rescue. The primary focus of the IAM solution revolves around managing data, identities and access maintenance throughout the lifecycle.
Core purpose which can be solved using IAM are:
- Identity Management – Management or governance of identities throughout the IAM lifecycle.
- Access Control – With the help of access controls like single sign-on and 2-3 step authentication.
- Directory Services – A common repository to manage user credentials in an organization.
- User Provisioning – It helps assign roles and access to new users automatically.
- Identity Maintenance – Is a safe way to mitigate the security threats by proper access management.
- Analytics – Use of machine learning for malicious threat protection before the damage is caused.
- Single sign-on – The management of user ID/passwords for a single account for simplified services.
- Authentication – It is important to check the authenticity of the users logged into a system. This can be two or three step authentication (two or three layers of authentication).
What are the advantages of Identity and Access Management?
Apart from security and business productivity, IAM solutions have three major benefits. They are:
Data Sharing
Identity & Access Management offers both identity and access management using a single platform. This helps reduce the time taken for managing separate solutions for both identity and access control. It is possible to have a common security policy across any device or platform in an organization. Some of the most commonly used policies in the IAM solution are around multi-factor authentication, access management and identity.
Usability
When it comes to usability, IAM is an efficient solution for sign-in and managing multiple user access automatically. By using this system, administrators can easily assign access controls automatically and reduce human efforts and errors simultaneously.
Cost-Effective
Enterprises take a lot of efforts to reduce operating costs and try to find better tools from time to time. With IAM, users do not require local identities for external users which assists a smoother admin process. You can get rid of your expensive on-premise hardware if you invest in Oracle Cloud IAM.
How to manage compliance with Identity and Access Management?
As a successful enterprise it is evident to comply with regulatory standards and industry standards. If there are no prevention measures taken by the organization, the time of audit can be overwhelming and can create issues that you were looking to avoid in the first place. IAM solutions help organizations in meeting their compliance goals. Europe has a GDPR compliance which is similar to the HIPPA and the Sarbanes-Oxley Act in the US for data compliance. If you use an IAM solution, you must be rest assured that all security standards are maintained. Essentially, it would help improve business operations and productivity of the teams.
Conclusion
As we come to the conclusion of this blog, we are sure that you must have understood the basics of Identity Access Management, the features and benefits involved along with compliance procedures to be followed. Now, Oracle Identity and Access Management can be easily used remotely by multi-factor authentication. The best part about investing in IAM, there is no upfront cost attached. It comes with on-demand pricing and is a cost-efficient cloud solution for most enterprises. Are you looking to strengthen the security of your organization and enhance business productivity? Get in touch with us at Conneqtion Group today to know more about Oracle Identity and Access Management solutions.


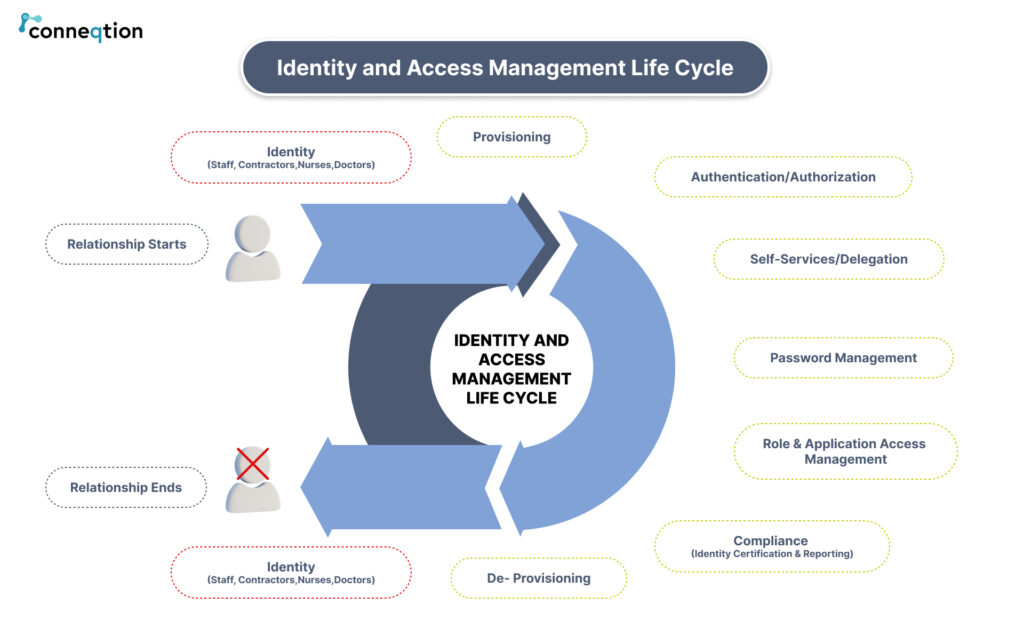
How To Configure Custom Endpoint of any Oracle VBCS application?
[…] 5: Create an Identity and Access Management (IAM) policy to Allow the integration service to read the version and contents of the secret and […]