Table of Contents:-
1. Asset Inventory
2. Data Encryption
3. Tracking & Auditing
4. Micro-segmentation
5. Implement Multi Factor Authentication
6. Data Protection Policies
7. CASB Methods
8. Compliance Management
9. Cloud Governance Strategy
10.Train Your Employees
In today’s digital age, data is king. But with great power comes great responsibility and protecting that data from cybercriminals is critical. Data breaches are a constant threat, and the cost is staggering. According to IBM’s Cost of a Data Breach Report 2023, the average total cost of a data breach hit a record high of $4.35 million. Even small businesses are not immune, with breaches costing an average of $2.4 million.
Here are 10 ways you can combat data breaches and safeguard your business:
1. Asset Inventory
Transparency of your current hardware and software assets in the network and will enable you to understand your business’ security condition better. Asset inventory can also be used to develop categories and ratings surrounding the threats and risks your assets may encounter from time to time. These categories and ratings will assist you prioritize the cleanup process that will happen on these assets.
Data breaches place a growing focus on endpoint protection. A simple antivirus may not be enough to avoid a catastrophic data breach for your organization. As a matter of fact, if you depend on anti-virus protection you will expose your desktops, systems and laptops etc. Laptops and desktops can be a significant pathway for data breaches.
An integrated endpoint solution like Oracle ERP Cloud security will leverage encryption to prevent data loss and leakage, apply unified data protection policies around your organizations’ servers, networks, and endpoints. This will reduce the risk of a data breach by 50%.
2. Data Encryption
Data encryption is a commonly used term in the software domain. When it is used correctly, it can provide an extra layer of security to your data. Data must be encrypted when it is stored in the cloud and even when it is being transferred to the cloud.
Businesses generally spend time and effort into data encryption only at rest. When it is stored, there is a greater potential of data breach due to possible threats. If you are looking to secure your data and avoid breaches, it is critical to address your data encryption at rest and in motion. You can also motivate your employees to reset passwords regularly.
Moreover, encrypting sensitive data enables you to avoid malicious threats from accessing customer or internal business information using strong cryptography algorithms. Safeguarding information at rest is crucial and makes sures that you use the latest encryption technologies like Salsa20, Two fish, AES-GCM, and ChaCha20-Poly1305.
3. Tracking & Auditing
CASB enables a business to use its tools to track, audit, and alert users. This empowers businesses to identify which users and networks are using your public cloud data, which helps you evaluate the dangers and handle all possible security challenges. With the help of diligent alerts, it is possible to find out more about security vulnerabilities.
It is important to complete the background check on your team. This includes allowing access to particular teams and rejecting access to others. Temporary employees and vendors must not be able to access the sensitive data on employees or clients. It is crucial to trust the appropriate people for the job when your business is subject to sensitive data.
Lastly, all the vendors must adhere to a company’s privacy policies along with general privacy laws. It means the vendors must abide by the background check rules.
4. Micro-segmentation
Micro-segmentation is just a new term that is used excessively in the IT industry. It is applicable especially to cloud communications and data storage. It allows network communication or access to those areas that need communication internally. This helps in reducing the dangers when you can cut your network access to a few specific devices. If not, you just leave the network open with a security concern.
It is one of the best policies to enable just enough access or JEA. The users will have just the required access to the resources they need. It means reducing employees’ device usage to strictly business use and stopping unauthorized websites.
It is best to limit access to resources and your business will do well to avoid the risk. Firstly, it is not a great idea to leave your computer unlocked when not in use. Also, bear in mind to not use Wi-Fi networks in public as data can be intercepted. Make sure the computers are password-protected, and have the computers ask for a re-login regularly due to inactivity.
Also Read: Data Quality: 4 Proven Methods for Evaluating the Health of your Data
5. Implement Multi-factor Authentication
6. Data Protection Policies
Use Oracle Integration Cloud security security best practices as well as privacy policies within your organization in order to protect your customers’ private information from being shared within the company. Consider adopting industry standards and best practices such as ISO 27001 or NIST 800-53, which focus specifically on IT security controls.
7. CASB Methods
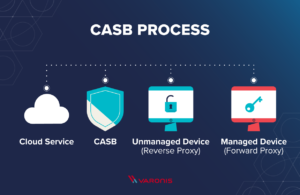
Closed access security broker (CASB) techniques are processes diligently managed by APIs and can be installed for small or large use cases. It supervises the network activity and reduces any activities that seem high-risk including downloading files and transferring the information on the internet that is not jeopardized. Most businesses that use cloud storage know and typically use CASB systems. It is available on a per-user basis so you have the same security criterias irrespective of the device you use to use the cloud.
Moreover, keep only what you actually need. Try not to waste hardware and software space on extra documents, files etc. Maintain your storage place when handling personal private data, and know where to store the data.
8. Compliance Management
A vulnerability and compliance management (VCM) tool in the workplace or conducting a vulnerability assessment will help you determine the gaps, weaknesses, and security issues in your digital and physical environment. VCM has the ability to relentlessly monitor the infrastructure and IT assets for security loopholes and compliance issues.
Some of the advantages that will assist to reduce a data breach include enabling your security team to identify the security concerns in the workplace. A great VCM will help you devise a plan of action to avoid these vulnerabilities and designate them to concerned team members.
9. Cloud Governance Strategy
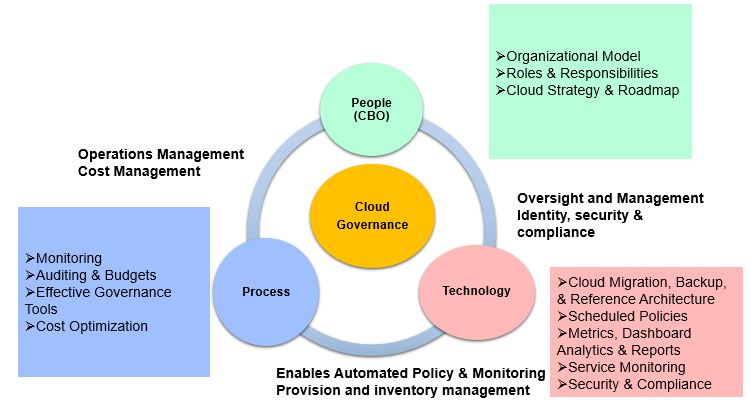
Certifying a cloud application is not the end, it is just the beginning. Your business needs an appropriate Oracle Integration Cloud security governance strategy and measures in place to ensure you are complying with data privacy directives (including your own and external). Educate your staff on this strategy and conduct timely checks and risk assessments so you are right on top of security.
Furthermore, transparency is a prerequisite, specifically if your business is run by the government. Following up with a cybersecurity response plan assists the employer and the employees to identify the potential risks in case of future data breach. Privacy is key to both companies and users, hence employers must remain transparent to both the internal and external stakeholders. It will help you save on lost productivity and avoid negative publicity.
Lastly, the response plan must include an evaluation of the current damages and when it occurred. It might be difficult to find out the exact cause of the breach straightaway, but it is a good place to identify the responsible party. The idea here is to take quick, definite action so a breach doesn’t reoccur. Once you know more about the details of the data breach and how to avoid them, it is easier to make informed decisions. And if your clients see that your business is dedicated to avoiding cyber-theft, it can make them feel comfortable and instill their confidence in your business.
10. Train Your Employees
After fulfilling your security audits, it is possible to circulate a detailed employed policy concerning data privacy and security. The business needs to conduct timely training sessions so that all employees are aware of the privacy policies. Before you establish a written security policy, look at some of the important points like:
- Limiting end user access and privileges as it is linked to the common policy “least privilege”.
- Use of unique passwords on computers, desktops and other company devices.
- Enforce a documented system for outgoing employees, and vendors or contractors.
- Educate employees on the significance of reporting strange data security leakage or breach.
- Make a policy that explains how employees must handle, dispose of, retrieve, and transfer data.
Employees require training on the kind of contemporary phishing attacks. As mentioned in a ransomware blog, phishing is one of the most popular ways for ransomware to spread in a business. Your organization will be ahead of data breaches if the employees have timely training about possible security indicators.
It is best to appoint an ambassador in your business that can head and conduct information security training sessions for your organization.
Conclusion
In the wake of a major data breach, your company needs to be prepared. You should determine your current exposure to cyber threats and attacks, develop security policies and procedures, evaluate the effectiveness of your existing security environment, and take steps to protect valuable assets. It may look like a tiring job to avoid data breaches. But, if you follow a secure approach with proactive measures and policies, your business will be in a much better position to mitigate security threats. In other words, you will need to have a solid security plan in place and make sure it works.
Here’s another blog which you can check: Cloud vs On-Premise ERP: Which is the right option for your business in 2022?
For more updates, please follow us on LinkedIn.

